What is Cloud Directory Posture?
The Cloud Directory Posture scans the activity and configurations of all users and inboxes and generates alerts in the platform. Detections include abnormal login locations, suspicious mailbox rules, and more.
Activating the Cloud Directory is the first step of the Guardz onboarding process and is crucial to activating many subsequent security controls
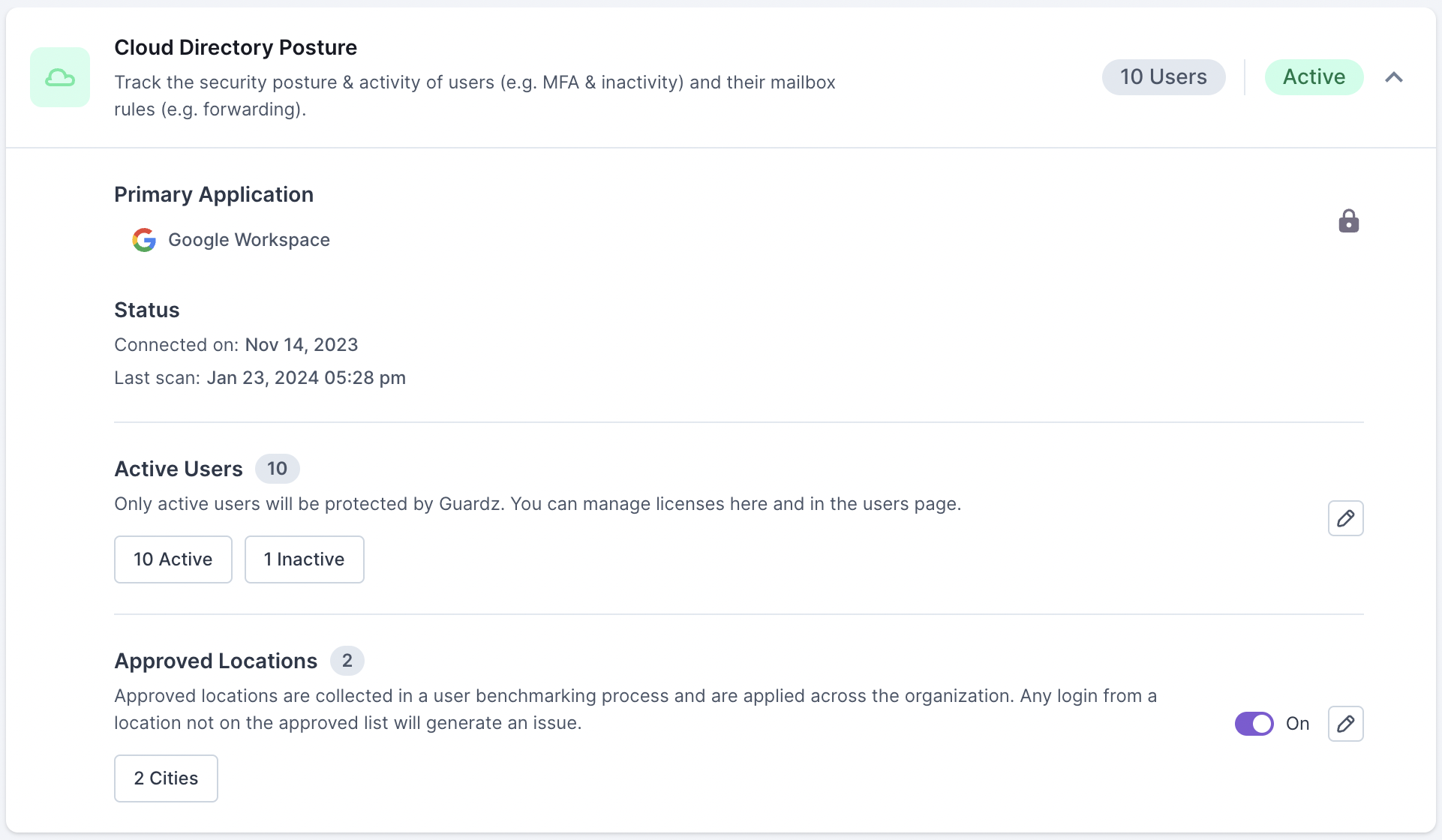
The Cloud Directory Posture is located in Security Controls > Cloud Directory Posture. Here you have an overview of the primary applications, the number of active users, and the number of approved user locations.
In the Single Customer view, you can:
Change license allocations
Activate the Approved Locations tool
View and edit the Approved Locations list
Approved Locations and Abnormal Logins
Guardz scans the primary cloud app activity and, based on a series of telemetry and metadata, builds a benchmark list of “normal” user login locations over 7 days of activity from historical logs. Guardz then identifies any logins outside that norm as “abnormal.” Abnormal Logins is a key protection against potential account compromise or outright account takeover.
In Security Controls > Cloud Directory Posture (Single Customer view), you have an overview of the list of Approved Locations. From here, you can turn the tool on and off. To view and edit the list of Approved Locations, select the edit icon.
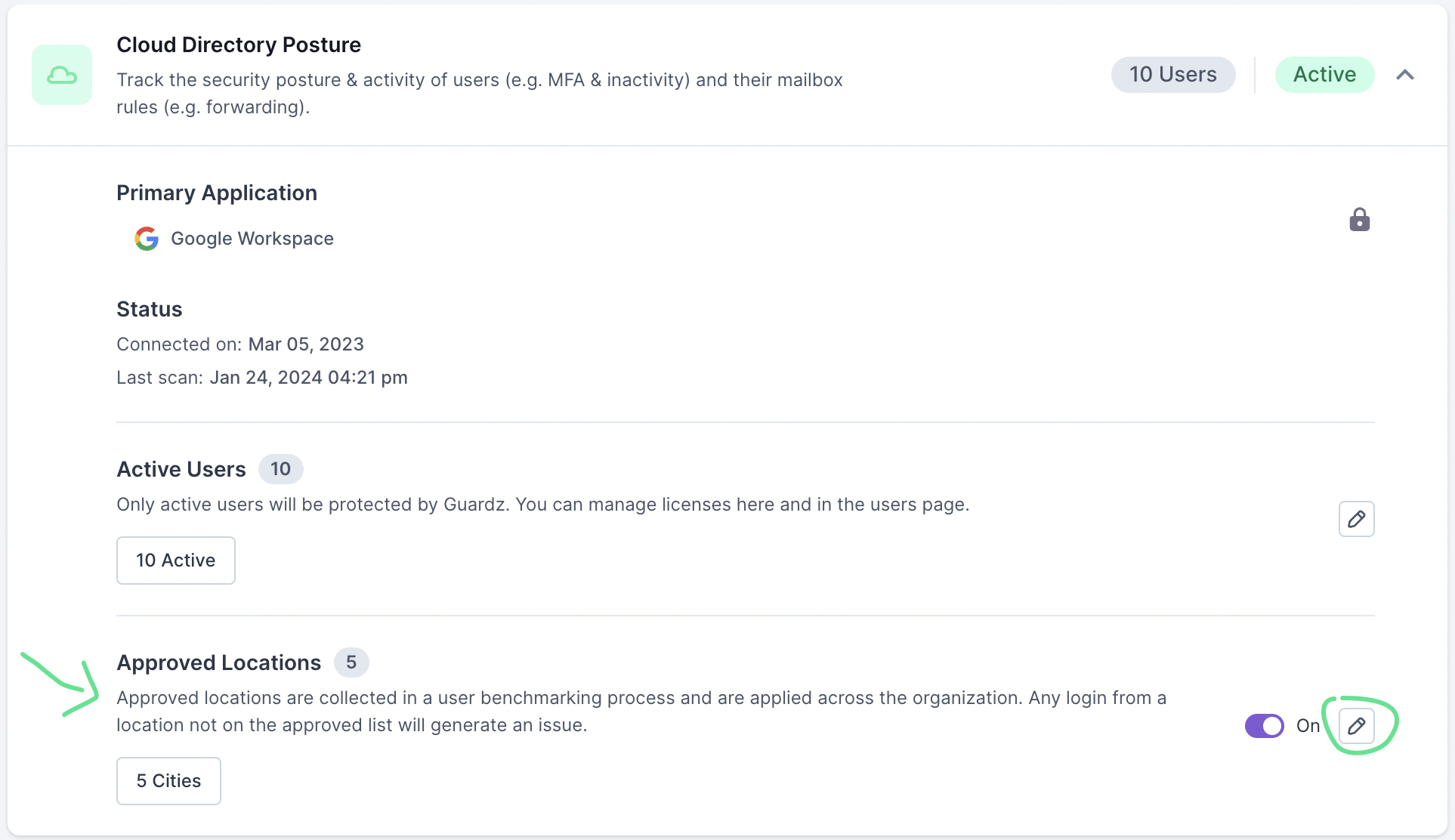
The list of Approved Locations represents the typical logins across an organization and can be viewed on a map as well as searchable, detailed list. Any logins detected outside these approved locations will result in the creation of a security issue.
Note that the Approved Locations list is currently based on:
IPs
Countries
Cities

You can add or remove locations from the list of Approved Locations, either through the issue remediation or “on-the-fly” in the Cloud Directory Posture security control. When a location is removed, logins from this location will no longer generate an issue, and any existing issue will be closed.
A location can be added with either the IP or the city and country.
If you want to take a more general approach, you can add a range of IPs. For example: 1.1.1.1/24 or select a country.

When adding a new location, the reason should be specified to differentiate between the system benchmark and admin approval.
FAQ Cloud Data Protection
Question: My user has MFA but an issue stating “MFA Missing Member” was generated. How is this possible?
?Answer: It is likely that the user needs to create a password for the MFA. This should resolve the issue.Question: How is the benchmark determined for normal logins?
?Answer: When you connect Guardz to your primary cloud app, Guardz will pull logins from the last 7 days of activity. Logins that occur more than 3 times from the same location will become the benchmark for normal locations.
Question: I'm having a problem enabling the Audit Logs
?Answer: in case you tried enabling the Audit logs and the insight appeared again, it might be related to the fact that you're using a Microsoft365 basic license. This capability is not supported in this plan.
Question: How is the severity of a suspicious login determined?
?Answer: If an admin user logs in from a high-risk country, it’s marked as Critical. If the login is either an admin user or from a suspicious country, it’s marked as High. Cases that don’t fit the above criteria are marked as Medium. If all detections are deemed safe by one of our benchmarks, it’s marked as Info.Info status is based on the following benchmarks:
User-Agent: If the user logs in from the same User-Agent more than 100 times in the past 30 days, it’s considered safe.
Device Agent: If a device from the same organization logs in from the same IP, it’s safe.
IP Reputation Score: If the IP has a reputation score of 0, it’s considered safe.
